Apple’s first pass at built-in encryption was, frankly, terrible. The original FileVault, introduced with 10.3 Panther in 2003, only encrypted a user’s home directory, and had a number of functional and implementation problems. FileVault 2 appeared in 2011 with 10.7 Lion, and had almost nothing to do with the original except the name.
FileVault 2 offers full-disk encryption (FDE). When enabled, the entire contents of the startup drive are encrypted. When your computer is powered off, the drive’s data is fully unrecoverable without a password. It also lets you use Find My Mac to wipe your drive in a matter of seconds remotely if you’re concerned about into whose hands your computer has fallen. You can enable FileVault 2 with an existing Mac, but starting with 10.10 Yosemite, OS X now encourages turning on FileVault 2 during setup of a laptop.
This has made some law-enforcement officials unhappy, who seemingly don’t want your data to be protected this strongly, so they can get access in the unlikely event that they need it. Relatively few people engage in criminal activities, and of them, even fewer ever have their computers seized and examined. It’s a good sign as to how well FileVault 2 works that officials are so morose about it.
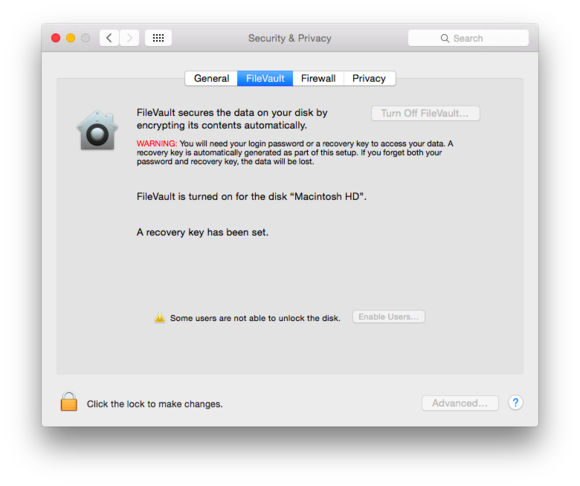
FileVault is easy to enable in System Preferences > Security & Privacy, and then once the intial encryption is over, it won’t even slow your Mac down day to day.
FileVault 2 takes advantage of the ever-improving processor speed and features in Macs to perform on-the-fly encryption and decryption. Every chunk of data read from and written to disk, whether of the spinning variety or SSD, has to go through this process. Macs introduced starting in 2010 and 2011, and every model since, can use encryption circuitry in the processor, boosting performance.
FileVault 2 works hand in hand with OS X Recovery, a special disk partition that lets you run Disk Utility from the same drive you may be having trouble with, restore or install OS X via the Internet, restore a Time Machine backup, or browse Safari. With FileVault 2 enabled, your computer boots into the Recovery volume, prompting you to login with any account that’s been allowed to start up the computer.
How to use FileVault 2
On a system without FileVault 2 already in place, you need to turn it on, which converts your startup drive from its unencrypted state to fully encrypted. This comes with a few big flashing red warnings and pieces of advice before you proceed. (You can encrypt secondary and external drives by Control-clicking a drive’s icon and select Encrypt “Drive Name,” but it doesn’t tie in with login: you set a password for the drive, and have to enter it to mount it.)
Warning 1! During the setup, OS X creates a Recovery Key for your drive. As with Apple’s two-step verification for Apple ID accounts, this Recovery Key is critical to retain. Without it, if you lose or forget the account password to all FileVault 2–enabled accounts, your drive is permanently inaccessible. Keep a copy of the Recovery Key, probably printed out, for emergencies.
Warning 2! Once you start the conversion, there’s no stopping it. It has to complete, and it consumes CPU resources like mad, slowing down your machine and likely firing up the fan to high speed. Your computer also has to remain plugged in. The operation takes many hours. A friend’s niece accidentally accepted the option to enable FileVault 2 when upgrading to Yosemite a few evenings ago, and had her machine—needed for a computer-science class the next morning—slow to a crawl.
Apple provides step-by-step details in a Knowledge Base note, so I won’t repeat all of that, but will highlight the critical parts.
Only accounts enabled with FileVault 2 can unlock the volume at boot time after a cold start (when shut down) or restart. For accounts you don’t opt to enable, restarting or starting up will require an account with permission logs in, then logs out. If you’re helping set up FileVault 2 for a novice user who trusts you, you may ask them to create an account for you that would let you log in if they can’t.
Accounts that use an iCloud password for login do provide a way out if you forget or lose an account password, but also offers a security risk if someone obtains your iCloud account information. (During a Yosemite upgrade, you can choose this explicitly when enabled FileVault 2 by checking a box that reads “Allow my iCloud account to unlock my disk.” Oddly, Apple has no information about this option on its support site.)
The option to store your Recovery Key on Apple’s servers is secure, in that Apple apparently can only unlock the key given information you provide, exactly as it’s typed, including capitalization. It doesn’t retain enough information to unlock it independently. However, it does put the key in the hands of a party other than yourself, making it possible under the right circumstances for a government agency or ne’er-do-wells to legally or socially engineer access to your recovery key.
Once the conversion is complete, the startup drive is fully protected within the limits of exposure I note above.
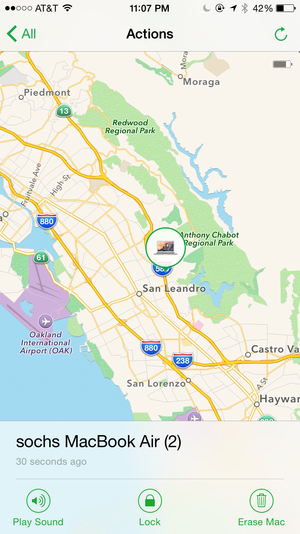
If you enable FileVault, erasing your lost Mac can be done in seconds, since the only thing it has to erase is your encryption key. But then no one can ever recover your data, not even you.
What’s even niftier is that with Find My Mac enabled on the computer, you have a sort of secret weapon. Find My Mac works when the computer is booted and connected to a network. You can play a sound, lock the computer, locate it (if Wi-Fi networks or other cues to location are nearby), and erase it. Because FileVault 2 relies on a stored encryption key, erasing the drive wipes that key, rendering the drive unrecoverable, even by you.
But the extra-secret secret weapon is Guest mode. When a user logs in as a guest and connects to a network, or the Mac automatically connects to a known network, Find My Mac continues to work. Thus, if someone finds your computer, any message you send with the Lock option can appear, even if it was online before they log in as a guest. But so too can an Erase request make its way through silently.
FileVault 2 can make nations quake, apparently, but it’s just a bit of good information hygiene, letting you make choices about the degree of vulnerability you want to tolerate for your locally stored data and any software or stored passwords for services in your accounts. With it off, you’re not risking everything, but with it on, you have a high degree of assurance about who can access what.
