A Mac is not a fortress, but it’s remained resilient against the worst sorts of attacks that have plagued Windows over decades and Android over years. Ransomware and other malware routinely appears to target macOS users, but it typically requires something extra to move into play. We made a misstep in judgment, or we trust something is true that is not.
So that your columnist doesn’t appear to be looking down at mere mortals, I should note that I received a text message from DHL the other day about an upcoming package. I had, in fact, a package I was expecting from the UK, saw the link, and clicked it—and three-tenths of a second later hastily closed the browser tab that opened. My defenses were down, as I expected a DHL text.
A normal DHL text looks like this:
DHL Express 1234567890 from SENDER NAME. estimated Wed Jul 31. Manage delivery: https://delivery.dhl.com/US/adsfad Reply END to stop msgs
But the one I received said something like:
Hello, mate, your DHL package is attempting to deliver http://98098adfadfasd.alsdfjas.com/98adf098asf0adf9
The text shouldn’t have fooled me, but my normal skepticism was overridden expectation. So far as I know, this click wasn’t to a zero-day exploit that loaded—an unpatched bug used for high-value targets, typically—but to an ad. May I interest you in some fine beluga caviar, very cheap, or knock-off leather bags? Click here.
Anyway, it can happen to any of us, but we can prepare for the worst. Here’s how.
(If you are still doubting whether Macs get viruses read our list of all the malware that’s been seen the Mac.
How to stop malware getting on to your Mac
Typically malware or viruses get on to your computer in a handful of ways. You can help diagnose whether you might have an actual infection by seeing if you’ve undertaken any of these steps recently:
Also see: What to do if you think your Mac has a virus.
1. Avoid downloading malicious software
Apple has in-built protections that should stop you installing this sort of thing. The company won’t allow you to install software that isn’t from a registered developer, for example, without first jumping through a few hoops. When you try to open such an app you’ll see a warning that the application is from an unidentified developer. Of course, it’s not always going to be the case that this is malware, so it is generally possible to open such software, but you will have to make some changes to your settings in order to do so as we explain here: How to open a Mac app from an unidentified developer.
There are also protections in place that should mean macOS’s Gatekeeper technology that should recognise any malicious software and stop you from installing it – as long as it’s not very new (it can take Apple a few days or weeks to address new malware). Should macOS detect a malicious app it will let you know and will ask you to move it to the Trash. Read more about Apple’s built in virus protection here: How Apple protects your Mac from Malware.
However, the malware might have looked like legitimate software, such as a virus scanner that you download and installed in panic after believing yourself to be infected. Check for independent reviews of apps or ask for personal recommendations from others to avoid downloading this kind of thing.
This kind of malware might be downloaded by you, or it might arrive via email, or perhaps even arrive via an instant message.
To protect yourself we also recommend that you read about how Apple protects your Mac with these Mac security settings.
Don’t relax entirely in the comfort of knowing that Apple has your back. There are still ways that malicious software could fool you into installing it.
2. Be careful with fake files
Sometimes malware or viruses might be disguised as an image file, word processing or PDF document that you open either without realising what it is, or out of curiosity to see what it is – perhaps upon finding a strange new file on your desktop, for example. (Top tip: DO NOT open files that suddenly appear unless you know what they are!)
The malware creator’s technique here is simply to give the malware a fake file extension. Most of us can see straight through this, but it’s surprising how effective an attack vector this can be.
These kinds of files often arrive via mysterious emails from colleague that you later discover have had their email hacked.
3. Look out for malware-loaded via legitimate files
Malware can get on to your system via a flaw or security hole in your browser or other software, such as your word processor or PDF viewer. In such a case an otherwise ordinary document or webpage you open contains hidden malware that then runs without you realising, or opens a hole in your system for further exploitation.
4. Avoid fake updates or system tools
Malware usually looks like a legitimate update. Typically this is offered via a fake warning dialog box while you’re browsing. Fake updates for the Adobe Flash Player browser plugin, or fake antivirus/system optimisation apps, are a particularly popular vector of attack.
Note that Adobe ended support for Adobe Flash on 31 December 2020, so if you are invited to download the Flash Player don’t do it!
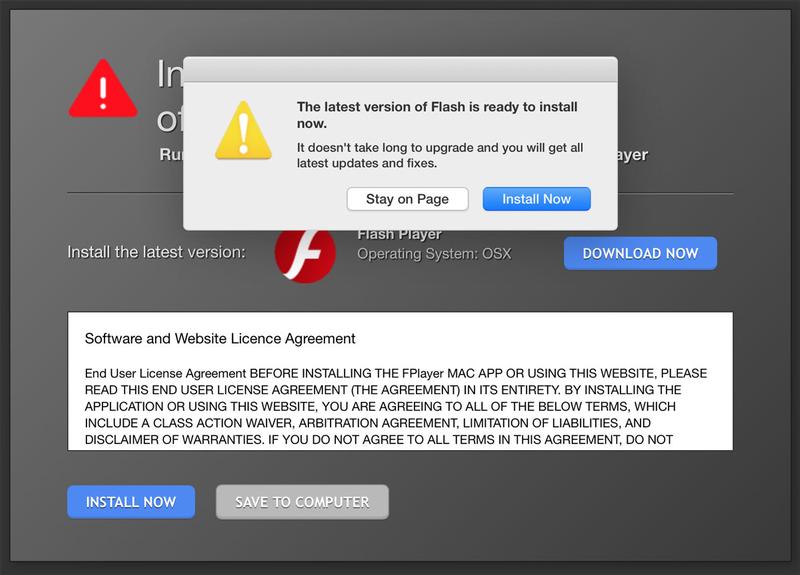
5. Don’t accept fake technical help
If you’re phoned out of the blue from Apple or Microsoft, maybe even BT, and they tell you that they believe your computer is infected, and offer to walk you through some steps to undo the damage don’t do it! They will be putting in place their own malware, of course.
6. Only run known software
The main conduit for malware on the Mac is software you download and install. Don’t click on links in email to download software. Don’t accept online recommendations for software from people and sites you don’t know. Google search results are polluted at the top with bad actors, unfortunately. If you limit software installations to that from the Mac App Store and from well-known developers, using downloads directly from their websites, you’ve eliminated most risk.
7. Beware adware
While macOS is so far resistent to self-installing malware, a category of apps called Potentially Unwanted Programs (PUPs) remains a burden. This is software that’s installed alongside a useful app because you might think it’s useful, and then it rewrites URLs in your browser or performs other activities that interrupt your computing (like a full-screen interstitial ad on your Mac!), but aren’t technically malware. Jason Snell
wrote extensively about this PUP danger recently. Apple is increasingly blocking these apps from running, but they’re still in wide use, and I routinely receive email from users who can’t install an app or find their Safari homepage hijacked. Like Jason, I also don’t recommend the routine installation of anti-malware software, because it offers little protection against Mac users’ biggest risks. If you routinely exchange files with Windows or Android users, however, anti-virus software is helpful in stripping malware that you might pass on, like a carrier, to those users if they don’t have AV software in place.
8. Don’t bypass macOS app protection
Apple allows developers in its program to submit and have their apps digitally signed, which sets a bar a bit higher than software that isn’t. Most people engaged in active development of free and paid software pony up the money to be in the program and get signed for their users’ reassurance. When you have an app that
makes you go through the extra steps to bypass this, think twice. (There are some very useful apps, generally free and updated through the goodness of volunteer programmers’ hearts, that aren’t signed. But you need to check the provenance very carefully on that small set of apps.)
9. Don’t click unknown URLs
Don’t be like me (see above) and click URLs that appear in messages or email unless you absolutely know the source of the message or email. I often type a known site’s URL in rather than click through to avoid being misled. Recently, the company where I rent a virtual private server (VPS) had a spate of fake emails not sent by them—but which looked shockingly legitimate—blanket the internet. I typed in their URL instead, and found the problem documented on their blog. (They hadn’t leaked any email addresses. It was just massive spam.)
What to do if you are attacked
If the worst happens, remember:
- The best response is to wipe and restore from your most recent unaffected complete backup—typically one that’s offsite, but which may be a rollback on Time Machine. You can spend a lot of time playing whack-a-mole to eradicate a problem. A clean reversion is your best strategy.
- If attackers render data on a drive unusable, turn to an
Apple consultant,
DriveSavers, or other firms that specialize in recovering lost data. - Don’t blame yourself for being a victim of an attack. Hundreds of thousands, maybe millions of people around the world spend their days and nights trying to find your weakness. Blame them!
Prepare for the worst and make backups!
Make backups. Make backups. I’m a broken record, but it’s the single easiest and best thing you can do. With multiple backups, even if someone manages to corrupt your machine, infect it, or delete files, you will have some way to recover.
Use the 3-2-1 strategy described in this previous column. Generally, have a local backup, have an offsite one you rotate through, and have a secure online archive.
