Despite the rise of two-factor authentication, password security remains a top priority. Unless your password is unique, relatively long, and hasn’t been found in a database breach as plain text, you should probably change it. For some sites, you might not have changed the password in years–or ever. (Conversely, if any password for a given site you use is unique, long, and unbreached, there’s no valid reason to change it.)
Apple offers a tool to help you fix your worst passwords. Security Recommendations can be found in iOS/iPadOS in Settings > Passwords. In macOS, find it in System Settings > Passwords (Ventura); or System Preferences > Passwords (Monterey); or Safari > Preferences/Settings > Passwords (all macOS versions). It’s easiest to manage on macOS, so the examples below come from Ventura.
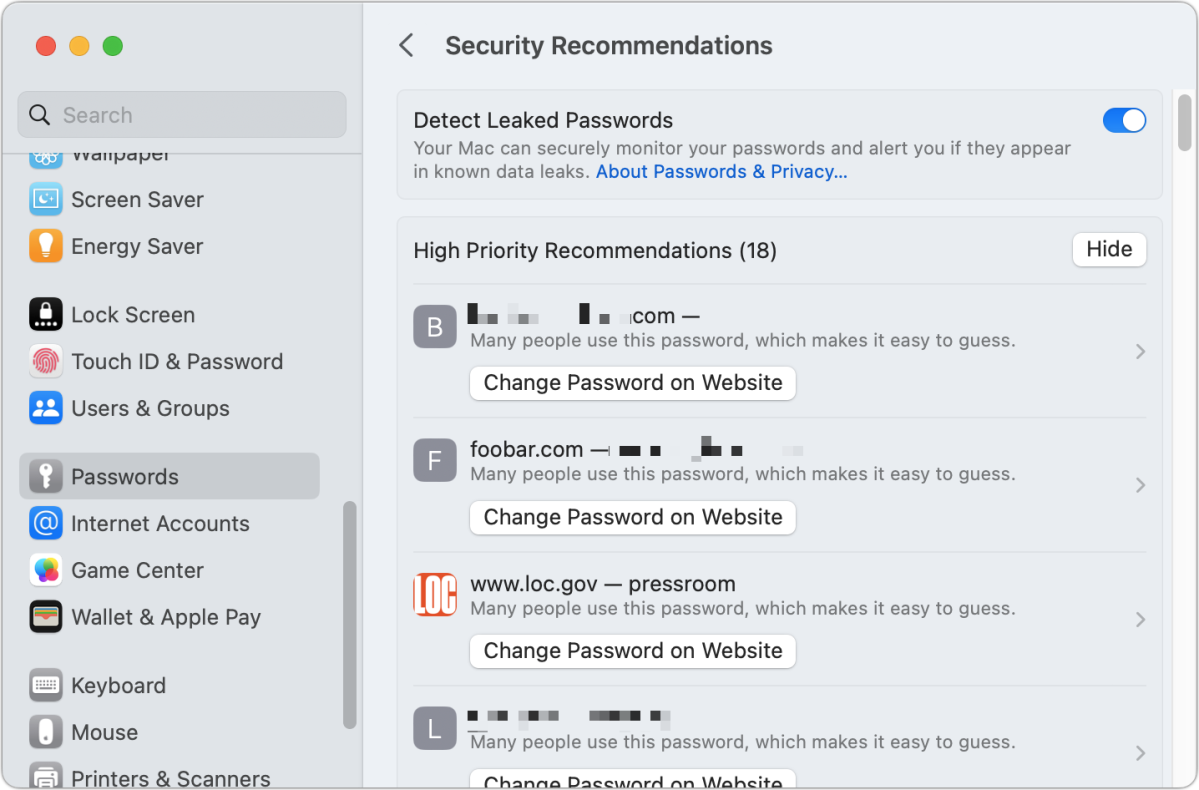
The recommendations are divided into High Priority Recommendations and Other Recommendations. For me, I had 18 in the former category and 68 in the other. (If you don’t have any High Priority Recommendations, it may just show a list.) It’s not clear why Apple promotes some entries into the high-priority category. With my account, items listed as high priority include a financial site, a government (.gov) site, and several Apple sites. The other sites included don’t necessarily have anything in common–possibly the shortness of the password or how commonly used a word in the password was.
Warnings listed by Apple
Here’s what you’ll see as warnings in both high-priority and standard-priority entries:
Commonly used password: Passwords identified as commonly used come from the result of years of password leaks. Passwords used by many people can now be easily found on the Internet by anyone, much less criminals or other attackers. Apple notes, “Many people use this password, which makes it easy to guess.” I’ve found a number of test accounts in this category—accounts I set up and never used or that were set up for me temporarily. The passwords have been as poor as the letter a and the word password. (These matches are made via information Apple stores on your computer.)
Crackers who gain access to an account database that lacks proper modern protections that render identical passwords as unique cryptographically obscure entries will run a list of the most commonly breached passwords first. This lets them find low-hanging fruit.
Commonly used word. Apple warns you if you’re using a common word, one that’s short and in frequent use in your language. Password crackers used to run through common words to crack passwords; that may be outdated because of changes in how passwords are stored. But it’s still unwise to have a password that’s all or mostly a common word.
Database leaks. Passwords specifically found in database leaks, whether common or not. Apple’s explanation is that “This password has appeared in a data leak, which puts this account at high risk of compromise.” These matches are made remotely by Apple against data from breaches compiled by reputable security sources that Apple has licensed, acquired, and stored using a clever cryptographic approach that prevents them from transmitting your exact password. Their list contains 1.5 billion passwords. You can opt out, however, by disabling Detect Leaked Passwords.
People attempting to break into accounts will also use less commonly found passwords depending on the computational resources they have available. If a password you use (you alone or also by other people in the world) has ever leaked as plain text, you can’t be sure that someone can’t attack your account with it.
Reused passwords. Apple notes this for passwords that you use across multiple sites. The text reads, “You’re reusing this password on “domain“, which increases the risk to this account if your “domain” account is compromised.”
Once, it was common wisdom to pick a strong password–at the time, one that was a random sequence of 8 characters, later as long as 12–and use it everywhere. The advice was to change it from time to time. That advice expired long ago. Now, you should use a password manager, like the built-in one in Apple’s operating systems, to create and store a unique, long password for every site and service at which you register.
How to upgrade your password quality
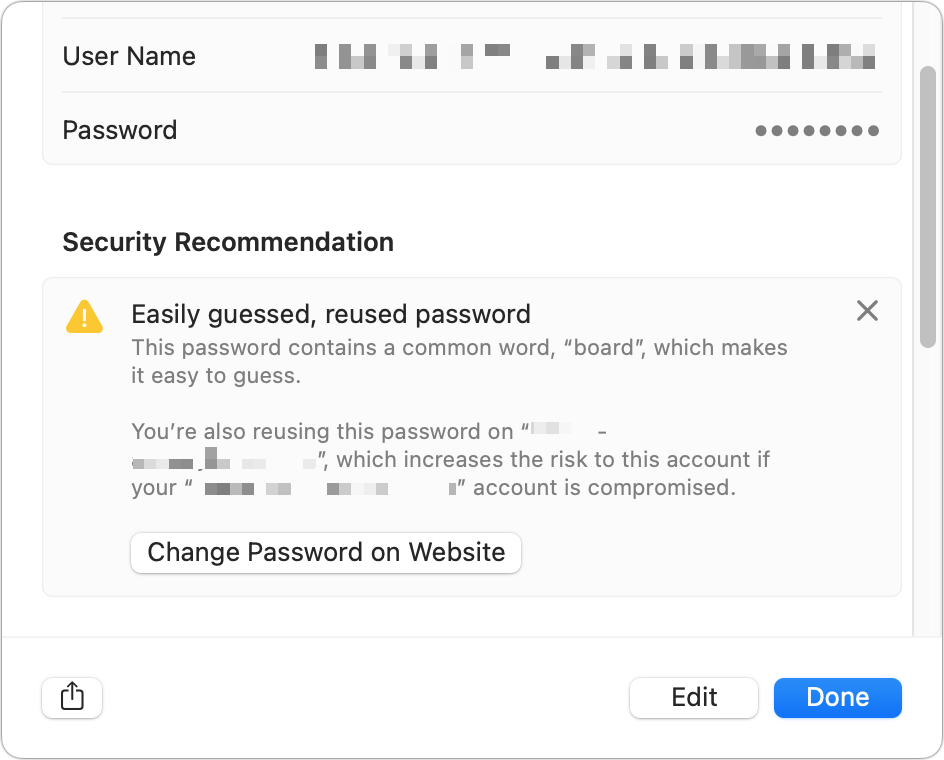
Apple has a shortcut that lets you change a weak or compromised password quickly. For high-priority entries, click Change Password on Website; for other entries, first click the entry and then click Change Password on Website.
This may take you to the change password or account-management page on the site. Apple developed a specification that allows a website operator to put a specially formatted file (or use a script to do the same) at https://example.com/.well-known/change-password that redirects to the correct page. If that location exists, clicking the Change Password on Website button takes you to the right spot; if not, it takes you to the site’s home page. (If you run a website of any size, it’s very easy to set up.)
If you change the password on the website using Safari, you’ll be prompted to update your stored password in the keychain.
You can also modify the password directly in place and then copy and paste it into a website. You can click Edit and then click Create Strong Password, and the password manager generates a new, better one. However, you might need the old password to log in–so make a note of the old password first before updating it.
This Mac 911 article is in response to a question submitted by Macworld reader François.
Ask Mac 911
We’ve compiled a list of the questions we get asked most frequently, along with answers and links to columns: read our super FAQ to see if your question is covered. If not, we’re always looking for new problems to solve! Email yours to mac911@macworld.com, including screen captures as appropriate and whether you want your full name used. Not every question will be answered, we don’t reply to email, and we cannot provide direct troubleshooting advice.
